Prevention Strategies for Cybersecurity Attacks on Advanced Medical Devices
Healthcare data security has been a concern since the early days of electronic health records.
Over time, healthcare delivery organizations (HDOs) built up huge databases of patient data. When the internet arrived on the scene, those databases became lucrative targets for hacking.
Today, the growth of connected medical devices is further straining early systems that were not designed to secure data from distributed networks.
The challenge remains the same: How to balance protecting sensitive data while allowing providers to efficiently share patient information in order to coordinate the best care.
And, it’s not just new devices that pose risks. Older devices may contain outdated software and firmware that makes them susceptible to exploitation through illicit access, unapproved changes in configuration settings, or stolen credentials. Much like old consumer electronics gadgets, older units may “age out” with unsupported software.
As connected medical devices flood the marketplace for inpatient and outpatient care, data loss risk increases. Click To TweetCybersecurity specialists often use the term “attack surface”; the growth in connected medical devices creates a larger attack surface for hackers.
Not only do cybersecurity attacks pose a risk of financial damages due to data and identity theft, but they can also endanger patient well-being or even lives if devices malfunction or deliver incorrect treatments.
Let’s look at some of the issues surrounding cybersecurity and advanced medical devices.
Regulatory Positioning for Medical Device Cybersecurity
We start with regulatory issues because medical devices must pass regulatory scrutiny to enter the marketplace in the first place.
In the United States, the FDA clarifies cybersecurity responsibility on its website:
Medical device manufacturers (MDMs) are responsible for remaining vigilant about identifying risks and hazards associated with their connected medical devices, including risks related to cybersecurity.
The FDA has outlined regulations for medical device manufacturers to ensure the safety and security of patients’ personal data. The guidelines clarify how manufacturers can comply with their responsibilities.
Recommendations include incorporating additional measures such as risk assessments, software engineering controls, authentication protocols, encryption methods, and data segmentation into their product design and development.
Additionally, the FDA requires manufacturers to develop detailed policies and procedures regarding device security that cover a range of topics, including incident response procedures in the case of a breach or other adverse event. Having a plan for documentation key.
With cybersecurity and regulatory compliance as ground zero, let’s look at some best practices for security and connected medical devices.
Medical Device Cybersecurity Planning in the Design Phase
Include cybersecurity expertise from the start
The medical device development plan needs to integrate cybersecurity considerations from the start. This means including experienced programmers with cybersecurity expertise on the team.
Another tactic is to implement a Threat Model early in development as a resource to model threats, responses, and prevention.
Design for the whole product life cycle
Secure connected medical devices require maintenance, monitoring, and updates across their lifecycle. The FDA encourages continuous vulnerability assessment and penetration testing throughout the device lifecycle to minimize security flaws or vulnerabilities.
Advanced medical device manufacturers need to plan for a continued relationship with clients after the sale, supporting security for the entire lifecycle of the product.
Someday, the new device will be old, and the manufacturer will still need a security plan. For example, the FDA already wants to see action plans for timely patch updates for older devices.
Mitigate exposure risk from vendors
The FDA is clear that the MDM is responsible for the performance of any software included in its product, whether developed in-house or not. Carefully vetting off-the-shelf (OTS) software code or third-party vendors for cybersecurity considerations is crucial. Data management is a significant consideration. Look for experienced, regulation-compliant solutions for cloud data storage with analytics and active cybersecurity monitoring.
Understand HDO needs early
Large HDOs are beginning to screen medical devices for cybersecurity as part of the purchase decision for medical devices. For example, the Mayo clinic enforces a Proactive Security Model to screen Medical Devices for potential cybersecurity weaknesses.
For client HDOs, it is vital to implement an effective communication strategy for sharing updates with HDOs about any necessary changes to the product regarding its security features. Highlighting the communication strategy early in the sales cycle can also help build trust with prospects.
Finally, medical device startups should also note that connected medical device security is becoming a critical HDO requirement from MDMs. For that reason, advanced medical devices are stakeholders in HDO policies for data security even before GTM, purchase and deployment.
Medical Device Cybersecurity Prevention and Monitoring in the Marketplace
Once devices enter the marketplace, cybersecurity becomes a paramount consideration as exposure to wider networks increases. Let’s look at some post-launch strategies.
Preventive medicine via better data sharing training and controls
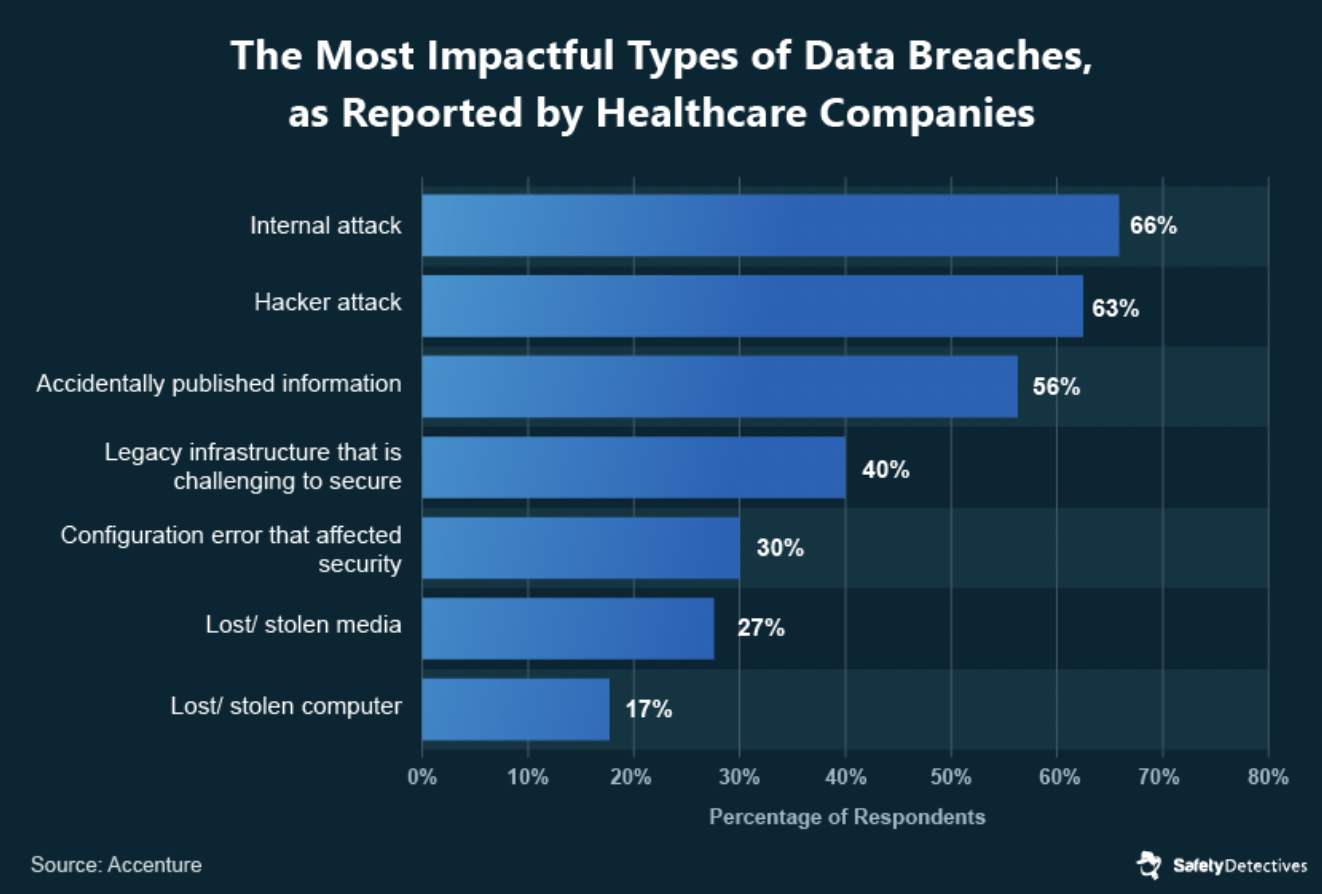
Even though malicious attacks make the headlines, a study by Accenture revealed that over half of significant breaches were from employees who accidentally published information. (By the way, accidentally leaked data is also a problem in the financial services industry, too.)
The FDA tasks healthcare delivery organizations (HDOs) to evaluate their network security and help protect hospital systems. To improve data security from advanced medical devices and other sources, advanced medical devices can work with HDOs to improve employee education about what kinds of data can be shared and when. Best practices and training are essential. Communication compliance and data loss prevention software can help companies enforce policies on sharing sensitive information.
Medical device security monitoring and updating
By taking proactive measures such as regularly updating software patches and monitoring potentially vulnerable networks, organizations can safeguard patient health and significantly reduce the chances of falling prey to these types of threats.
Another important step that medical device manufacturers should take is implementing periodic patching and updating software code to prevent the exploitation of known security flaws. This can help prevent new threats to vulnerable devices.
Furthermore, medical device manufacturers must also consider conducting regular penetration tests to identify hidden weaknesses in their devices’ security architecture.
Planning for the Worst Improves Outcomes
5-star general and former US President Dwight Eisenhower said, “I have found that plans are useless, but planning is everything.” What he and many corporate strategy consultants are referring to is that even though we cannot predict the future, we can increase the probability of better outcomes through planning.
Planning is a form of practicing. When people spend time preparing responses to different hypothetical scenarios, results in the real world improve.
When medical device teams create comprehensive incident response plans detailing responses to cyber attacks, breaches, or system outages, they practice solving problems ahead of time.
Finally, planning can result in improvements to existing systems. Walking through scenarios can reveal areas for preventive measures that teams may not have identified previously.
Moving Ahead
To achieve and maintain regulatory compliance, medical device manufacturers need to take measures to protect their devices from cyberattacks and data leaks. This is a moving target that requires careful planning and a robust team approach.
For a deeper dive, you can check out our CTO Abbas Dhilawala’s recent talk where he outlines privacy, security, and regulatory challenges, and present considerations that are critical for successful medical device connectivity.
At Galen, we have deep experience helping companies with compliance and cloud data storage considerations. Contact us today for a free consultation.